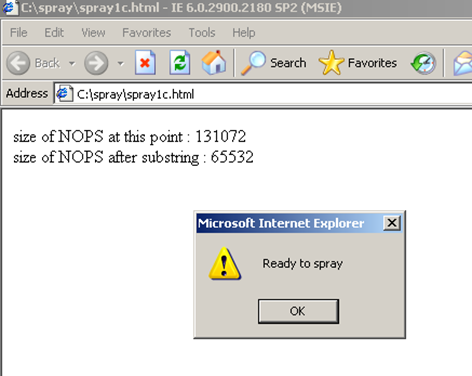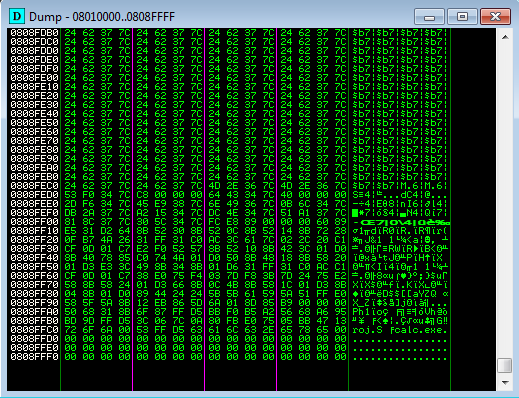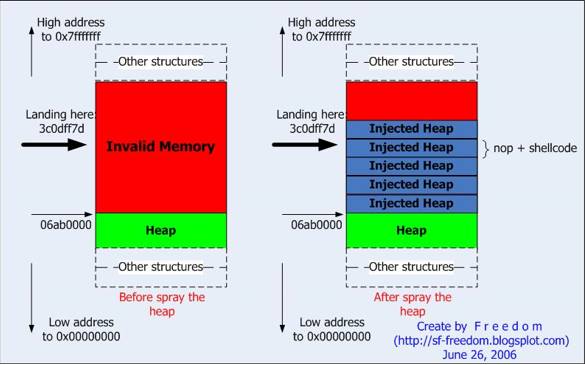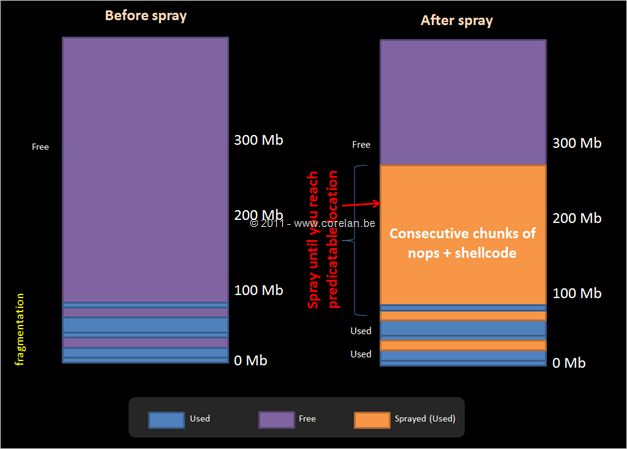
Exploit writing tutorial part 11 : Heap Spraying Demystified | Corelan Cybersecurity ResearchCorelan Cybersecurity Research

RandHeap: Heap Randomization for Mitigating Heap Spray Attacks in Virtual Machines | Semantic Scholar

Exploring the crypt: Analysis of the WannaCrypt ransomware SMB exploit propagation - Microsoft Security Blog

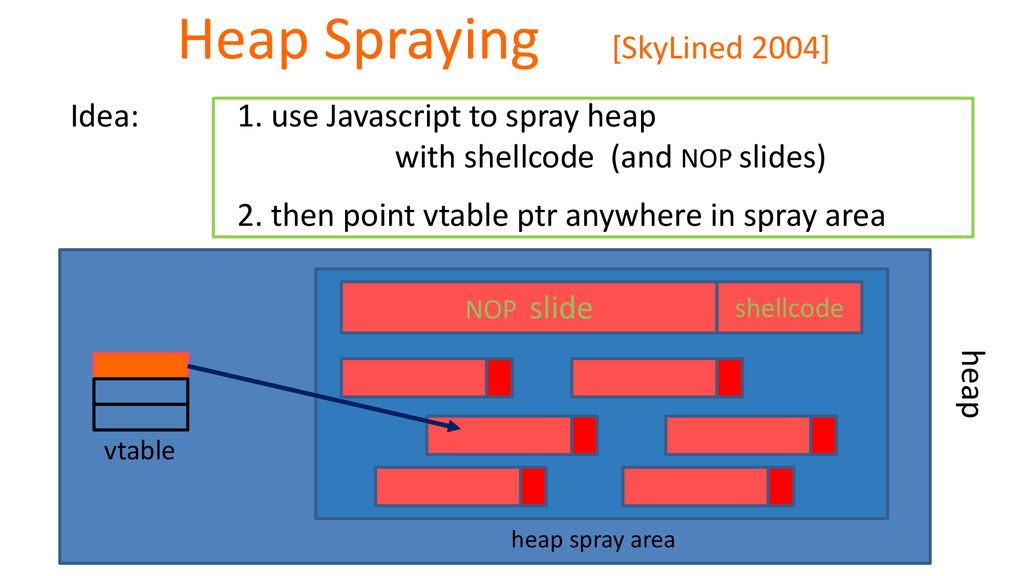
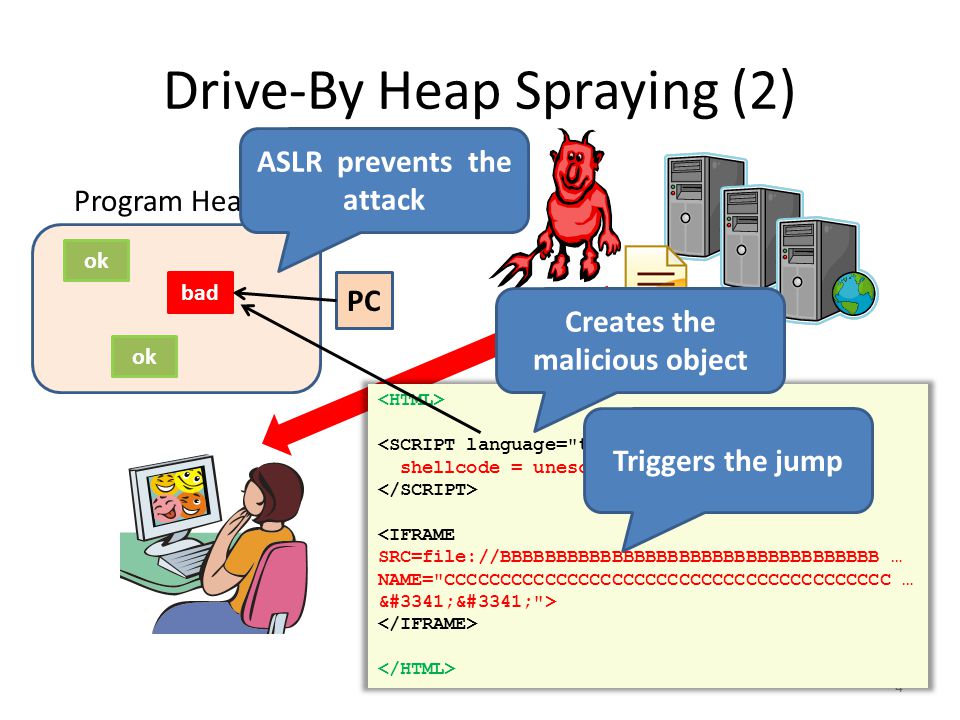
PPT - Nozzle: A Defense Against Heap-spraying Code Injection Attacks PowerPoint Presentation - ID:2510980

RandHeap: Heap Randomization for Mitigating Heap Spray Attacks in Virtual Machines | Semantic Scholar

RandHeap: Heap Randomization for Mitigating Heap Spray Attacks in Virtual Machines | Semantic Scholar

RandHeap: Heap Randomization for Mitigating Heap Spray Attacks in Virtual Machines | Semantic Scholar

Exploring the crypt: Analysis of the WannaCrypt ransomware SMB exploit propagation - Microsoft Security Blog